Bug Prevents Mobile Units from Performing Mammograms
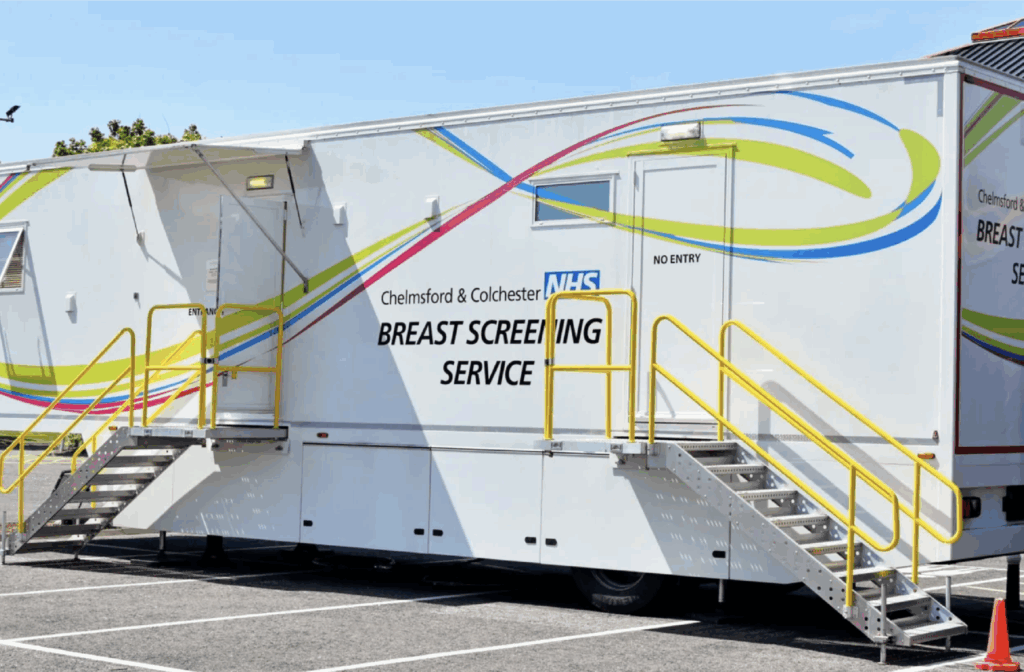
According to the BBC, thousands of women in the UK have been affected after breast cancer screening services were suspended in parts of Essex for two months. The vans and units covering the Colchester and Chelmsford areas have been out of service since early August due to a technical issue. Liberal Democrat MP for Chelmsford, Marie Goldman, described the situation as “simply not good enough.” Routine breast screening is offered to women between the ages of 50 and 71, and software problems in an image archiving and communication system were cited as the cause of the suspension of services. This system allowed new mammograms to be compared with previous images. Several women reported difficulties in booking appointments, being told that there was no availability. Christine Rhodes, from Chelmsford, said she tried to book an appointment four times but was unsuccessful: “My local online community group is full of concerned women who want to do the right thing but are being prevented from doing so,” she said. “We are talking about a condition that can progress rapidly and be fatal. If this unit is not repaired, the waiting list for screening will extend for many months. How many lives will be put at risk?” Healthwatch Essex noted that for many women, it can take courage to book an appointment and that the cancellation of appointments by services creates another barrier, which may prevent some people from receiving the screening or treatment they need. In a statement, ESNEFT apologized for the technical problems, which have now been resolved, ensuring that “around 7,000 patients will receive new appointments after their original screening invitation was canceled.” The organization also said it had “a recovery plan in place” and committed to seeing all affected patients “as soon as possible.” The original article via BBC here.
Bug Prevents Mobile Units from Performing Mammograms Read More "